Pointers & References: Double-Edged Sword of Memory Addresses
C's notorious barrier. Pointers directly manipulate memory addresses—powerful but dangerous. References are the safe version. The terror of Segfault and nightmare of nullptr.

C's notorious barrier. Pointers directly manipulate memory addresses—powerful but dangerous. References are the safe version. The terror of Segfault and nightmare of nullptr.
Why does my server crash? OS's desperate struggle to manage limited memory. War against Fragmentation.

Two ways to escape a maze. Spread out wide (BFS) or dig deep (DFS)? Who finds the shortest path?

Fast by name. Partitioning around a Pivot. Why is it the standard library choice despite O(N²) worst case?

Establishing TCP connection is expensive. Reuse it for multiple requests.

First C course, completely stuck on pointers. First systems programming assignment, couldn't understand why this simple code crashed.
int *ptr;
*ptr = 10; // Segmentation fault
"Why does it crash?" Program just died. Coming from Python and JavaScript, direct memory manipulation was a completely different world. I thought you just assign values to variables, but suddenly this "memory address" concept appeared, and the fact that uninitialized access kills the program was shocking.
More shocking was that pointers are the core of all high-performance systems—operating systems, databases, game engines. It was an unavoidable concept. I eventually accepted that without understanding pointers, system-level development is impossible.
It was a continuous stream of confusion. Especially the symbols had different meanings depending on context, making code reading confusing every time.
*? Isn't it multiplication?int *ptr and int* ptr?& and dereferencing with *?Symbols meant different things in different contexts. * means "pointer type" in declarations, "dereference" when used, and "multiplication" in arithmetic operations. Same symbol with 3 meanings felt like cryptography to beginners.
Understanding pointers came from a senior's "house address" analogy. This analogy clarified everything.
"Variable is a house.
- Value (10): Item inside house
- Address (0x1234): Street address of house
Pointer: Sticky note with address
- Follow note to reach house
- Write wrong address? Trespassing → Police (Segfault)
- Can change note to different house address (reassignable)
Reference: Nickname for house
- Call it 'my home' → points to actual house
- Can't manipulate nickname itself (not reassignable)
- No house can exist without nickname (initialization mandatory)"
After accepting this analogy, everything fell into place. Pointer is a sticky note with address, reference is a nickname for house. Sticky note can be changed to different house addresses, but nickname can't be changed once set. This difference was the essence of pointer vs reference.
I wondered why pointers are necessary. Can't we just use variables like Python? But I understood pointers are essential for three reasons.
First, hardware control. Operating systems must directly handle physical memory addresses. Hardware control like CPU registers, memory-mapped I/O, DMA is impossible without pointers. To manipulate hardware registers at memory address 0x1000, you need direct pointer access.
Second, performance. Copying large data when passing to functions is slow. Instead of copying a 10MB struct, just pass an 8-byte pointer. This is why C/C++ is still used in game engines and databases.
Third, dynamic memory. Often need to determine memory size at runtime. Need to create an array based on user input number? Must allocate on heap not stack, only possible with pointers.
Ultimately, pointers are tools for low-level control. This power was the core of systems programming.
int age = 25; // Variable: stores value (allocated on stack)
int *ptr = &age; // Pointer: stores address (ptr itself also on stack)
printf("%d\n", age); // 25 (value)
printf("%p\n", &age); // 0x7ffd5... (address)
printf("%p\n", ptr); // 0x7ffd5... (same address)
printf("%d\n", *ptr); // 25 (dereference: address→value)
Important here is stack vs heap distinction. age is automatically allocated on stack and automatically disappears when function ends. But dynamic memory is different.
int *heap_ptr = (int*)malloc(sizeof(int)); // Allocate on heap
*heap_ptr = 42;
// Heap memory doesn't disappear when function ends → free mandatory
free(heap_ptr);
Stack memory is automatic management, heap memory is manual management. Understanding this difference made it clear why forgetting free causes memory leaks.
*int *ptr; // 1. Declaration: "ptr is a pointer"
*ptr = 10; // 2. Dereference: "store 10 where ptr points"
int result = 5 * 3; // 3. Multiplication
Same symbol with 3 meanings. Initially confusing, but clear from context. In declarations it specifies type, alone before variable it dereferences, between two numbers it multiplies.
&int age = 25;
int *ptr = &age; // & = "get address" (address-of operator)
& is "address-of operator". Gets memory address of variable. This is the starting point of pointers.
int arr[5] = {10, 20, 30, 40, 50};
int *ptr = arr; // Array name = address of first element
printf("%d\n", *ptr); // 10
printf("%d\n", *(ptr+1)); // 20
printf("%d\n", *(ptr+2)); // 30
ptr++; // Move to next element
printf("%d\n", *ptr); // 20
This is pointer's power. Direct array traversal. ptr+1 doesn't simply add 1 to address. It increments by sizeof(int) (usually 4 bytes). Pointer type determines memory movement size.
This is why C arrays are fast. Python lists have many indirect references, but C directly traverses continuous memory.
void *generic_ptr; // Can point to any type
int age = 25;
generic_ptr = &age; // Store int address
printf("%d\n", *(int*)generic_ptr); // Explicit casting needed
void* is generic pointer. No type information, so casting needed before dereferencing. This is why malloc returns void*. To allow use as any type.
int add(int a, int b) {
return a + b;
}
int (*func_ptr)(int, int) = add; // Function pointer
int result = func_ptr(3, 5); // 8
Functions also exist somewhere in memory. Function pointers store that address. This is the foundation of callbacks. Asynchronous programming like JavaScript's addEventListener is ultimately function pointer concept.
int *ptr; // Uninitialized → garbage address
*ptr = 10; // ❌ Access random memory → program dies
// Correct method
int *ptr = NULL; // Explicitly initialize to NULL
if (ptr != NULL) {
*ptr = 10;
}
Uninitialized pointer points to random address. That address could be OS memory or other program memory. Accessing it causes OS to force-terminate program. This is Segmentation Fault.
Always initialize to NULL habit is crucial. NULL pointer dereference also crashes, but at least debugging is easier. Better than random addresses.
int *ptr = NULL; // "Points to nothing"
if (ptr == NULL) {
printf("Pointer is empty\n");
}
// ❌ Null pointer dereference = instant death
*ptr = 10; // Segmentation fault
NULL (or C++'s nullptr) explicitly indicates "invalid address". Used when pointer doesn't point to anything yet. Always NULL check before dereferencing is basic safe coding.
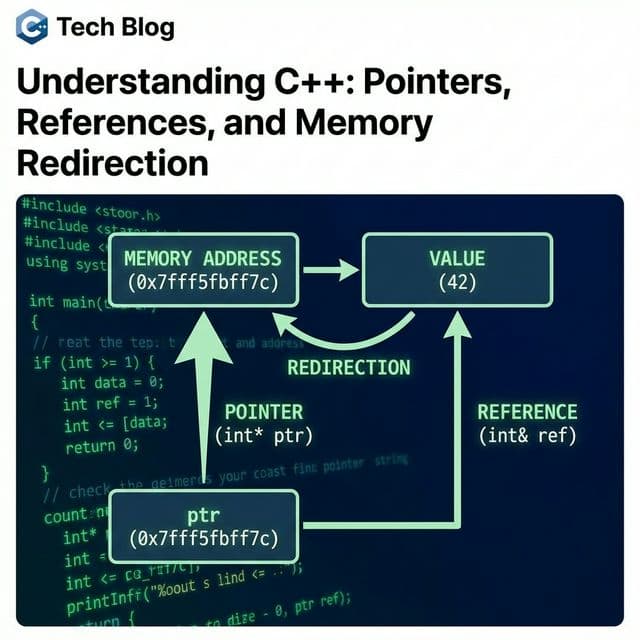
int age = 25;
int &ref = age; // ref is alias for age
ref = 30; // age becomes 30
printf("%d\n", age); // 30
Reference is variable alias. Stores address like pointer, but when used looks like regular variable. Direct access without dereferencing.
| Item | Pointer | Reference |
|---|---|---|
| Initialization | Optional (risky) | Mandatory |
| NULL possible | Yes | No |
| Reassignment | Possible | Impossible |
| Arithmetic | Possible (ptr++) | Impossible |
| Memory | 8 bytes (64bit) | 0 bytes (compiler optimization) |
// Pointer
int *ptr = nullptr; // NULL possible
ptr = &age; // Reassignment possible
ptr++; // Arithmetic possible
// Reference
int &ref; // ❌ Compile error: initialization mandatory
int &ref = age; // ✅
ref = another; // age = another; (not reassignment, value copy)
This difference matters. Reference once bound, forever that variable. Pointer can change to other variables, but reference cannot. ref = another; is not reassignment but same as age = another;.
// Call by Value
void increment(int n) {
n++; // Only copy increments, original unchanged
}
// Call by Pointer
void increment(int *n) {
(*n)++; // Original increments
}
// Call by Reference
void increment(int &n) {
n++; // Original increments (cleaner!)
}
int age = 25;
increment(age); // call by value → age = 25
increment(&age); // call by pointer → age = 26
increment(age); // call by reference → age = 27
Reference is cleaner than pointer. Can use like regular variable without * symbol. This is why C++ prefers references.
class Person {
String name;
}
Person p1 = new Person();
p1.name = "Alice";
Person p2 = p1; // Reference copy
p2.name = "Bob";
System.out.println(p1.name); // Bob (points to same object)
Java has no pointers. All objects passed by reference. But not C++ references, rather safe pointers.
list1 = [1, 2, 3]
list2 = list1 # Reference copy
list2.append(4)
print(list1) # [1, 2, 3, 4]
Python has no pointers either. Everything is reference. Garbage collector automatically handles memory management.
Java/Python "references" are not C++ references but safe pointers.
ptr++None, nullUltimately, C pointers with dangerous features (arithmetic, skipping initialization) removed. Safe but low-level control impossible.
int *arr = (int*)malloc(5 * sizeof(int)); // Create array on heap
if (arr == NULL) {
printf("Out of memory\n");
return -1;
}
for (int i = 0; i < 5; i++) {
arr[i] = i * 10;
}
free(arr); // Memory deallocation mandatory!
arr = NULL; // Prevent dangling pointer
malloc allocates memory from heap. Returns NULL if allocation fails, so always check. Deallocate with free, set pointer to NULL to prevent dangling pointer.
#include <memory>
// Raw pointer (risky)
int *ptr = new int(10);
delete ptr; // Forget = memory leak
// Smart pointer (safe)
std::unique_ptr<int> ptr = std::make_unique<int>(10);
// Automatic memory cleanup
Smart pointer uses RAII (Resource Acquisition Is Initialization) pattern. Automatically calls delete when leaving scope. Modern C++ recommends smart pointers over raw pointers.
valgrind --leak-check=full ./my_program
Valgrind is tool for detecting memory leaks and invalid memory access. Essential tool for C program debugging. Finds "where did I allocate memory but not deallocate?"
int* getNumber() {
int num = 42;
return # // ❌ Return local variable address
}
int *ptr = getNumber();
printf("%d\n", *ptr); // Garbage value or Segfault
When function ends, local variables disappear from stack. Return that address? Pointer points to already vanished memory. This is dangling pointer. This bug occurs intermittently making debugging hell.
int *ptr = malloc(sizeof(int));
free(ptr);
free(ptr); // ❌ Free twice → program dies
Free already freed memory? Heap structure corrupts. Subsequent malloc calls return wrong memory or program crashes. Can prevent with ptr = NULL; after free.
void leak() {
int *ptr = malloc(100 * sizeof(int));
// No free!
}
for (int i = 0; i < 1000000; i++) {
leak(); // Memory keeps leaking
}
Without free, memory not released. Keep calling function, memory keeps accumulating. Eventually eats all system memory and program dies. This bug is critical in server programs.
fn main() {
let s1 = String::from("hello");
let s2 = s1; // Ownership moves from s1 to s2
// println!("{}", s1); // ❌ Compile error: s1 no longer valid
}
Rust guarantees memory safety at compile time. Ownership system eliminates dangling pointer, double free, memory leak at source. Innovation maintaining pointer performance while ensuring safety.
func main() {
var ptr *int
num := 42
ptr = &num // Can use pointers
// But pointer arithmetic impossible
}
Go has garbage collector automatically managing memory but pointers exist. However pointer arithmetic impossible. Pursues balance between safety and performance.
This was it: Modern languages maintain pointer performance but remove or compiler-guarantee dangerous parts (arithmetic, manual management).
Understanding pointers gave me deep understanding of how computers work. Core lessons summarized.
NULL/nullptr. Random addresses are catastrophic.malloc comes with free. Forgetting causes memory leaks.Initially thought "Why made so complicated?" but after understanding the power of direct memory control, I accepted C/C++'s charm. Understood why OS, databases, game engines still built with C/C++. Pointers are double-edged sword. Use well for best performance, misuse for Segfault hell.